Introduction
The Research Group IT-Security of the RWTH Aachen University and the associated 0ldEur0pe CTF team are proud to announce the third incarnation of rwthCTF. rwthCTF 2013 will start on Saturday, November 9, 1400/2pm (CET) and go on for twelve hours (until November 10, 0200/2am (CET)). The intended audience are teams from universities around the world, but we can make exceptions for verified other organisations or institutions. Registration is closed!
Requirements
In order to participate, you will need a stable and relatively fast Internet connection (a few MBit/s in both directions are recommended). Also you will need a computer which is able to host a VirtualBox PC, i.e. a 64-bit host with VT-X technology. You will not need to travel anywhere.
You should know how to run a VirtualBox instance, set up a shared connection over an OpenVPN tunnel and know how to use PGP/GPG correctly. We expect you to handle your side of the OpenVPN setup yourself (that includes IPv6 inside our VPN this year). Please make sure that you know who's responsible for the VPN connection and the PGP keys on your team (we had some bad experiences with this).
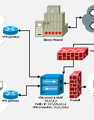
To get a rough idea of how a typical CTF network looks like, you can have a look at a poster we did about rwthCTF 2011. Feel free to post questions in our Google group or to @mention us on Twitter (hashtag #rwthctf). We will also be active in #rwthCTF on irc.freenode.net.
Follow @0ldEur0pe Tweet #rwthctf
Sponsors
Thanks to generous donations by our sponsors, we are able to offer cash prizes for the winning teams this year.
| Shopify is a commerce platform
that offers a professional online storefront, a payment solution, and
the Shopify POS retail application. Shopify currently powers over
60,000 online stores in over 100 different countries. If you like to break things for fun, and you're interested in working in a unique, large-scale environment where security and hacking on open-source software is a major focus, check out the Shopify careers page. |
RedTeam Pentesting offers individual penetration tests,
performed by a team of specialised IT security experts. RedTeam Pentesting is looking for new team members! |
| The UMIC Research Centre is a research cluster at RWTH Aachen University. It was established and funded as part of the German federal excellence initiative. |
FAQ
What is the root password of your vm images?
You are professionals, aren't you? Find a way out of your problem.
I lost my PGP private key or its passphrase. Can you help me?
Sorry, you're on your own. For security reasons we decided against key escrow.
Why can't we reach any machines from the VPN gateway?
Your VPN gateway is assigned a dynamic transport net IP address (for IPv4 and IPv6, each). Because this address is dynamic, we cannot derive your team ID from it. Consequently, transport network IP addresses are blocked in the firewall. Please use your team's networks for testing.
Why setup IPv6? We can connect via IPv4!
Plese note that IPv6 is REQUIRED in the game. Our gameserver will randomly contact your services via IPv4 AND IPv6. It will even change between the protocols for a flag PUT and subsequent GET.
Do we need an IPv6 uplink? Does our ISP need to provide IPv6?
No. The VPN connects via plain old IPv4, IPv6 is only routed within the VPN.
Can we setup a NAT at our VPN endpoint?
Traffic has to reach the vulnbox directly without any NAT or firewall. We don't care about the setup for your player's computers.
Are we allowed to firewall our vulnbox?
NO! You MUST NOT filter any traffic exchanged between the vulnbox and the VPN. If we detect that your vulnbox is firewalled, we may disqualify your team.
Participants (115)
 |
0daysober (-) |
 |
0xface8d (-) |
 |
1338-offbyone (FernUniversität Hagen) |
 |
1in9mu (itsystem) |
 |
2mr (2mr) |
 |
9447 (University of NSW) |
 |
aether shell (Imperial College London) |
 |
alcapwn (Universität Paderborn) |
 |
amir.a.r (isfahan university of technology) |
 |
anesec (University of Bologna) |
 |
asis (ASIS) |
 |
backzogtum (-) |
 |
bakunin (Swedish Royal Institute Of Technology) |
 |
balalaikacr3w (BalalaikaCr3w) |
 |
bi0s (Amrita University) |
 |
bitblaze (National University of Singapore) |
 |
bits for everyone (US Military Academy) |
 |
blakhole (Northeastern University) |
 |
blue-lotus (Tsinghua University) |
 |
botbie (f17) |
 |
brooklynt overflow (NYU-Poly) |
 |
bushwhackers (Lomonosov Moscow State University) |
 |
c14 (Amrita Viswa Vidyapeetham) |
 |
caspian (None) |
 |
catchmeifyoucan (TJUT) |
 |
cl0ud sh3llz (University of Michigan, Ann Arbor) |
 |
cookiemonsters (uoc.edu) |
 |
crazyrabbit (NA) |
 |
cwst (C0de&Web Sec Team) |
 |
darklapu (New Jersey Institute of Technology) |
 |
dcua (PTI NTUU "KPI") |
 |
defragmented brains (TU Wien) |
 |
delusions of grandeur (US Air Force Academy) |
 |
disekt (UGA/GT) |
 |
dodododo (dodododododododododo) |
 |
dotf (University of Regensburg) |
 |
dragon sector (-) |
 |
eindbazen (N/A) |
 |
elniepodlooxagic (ElniepodLooxAgic) |
 |
enoflag (TU Berlin) |
 |
entr0pia (University) |
 |
faust (University of Erlangen) |
 |
fear2fear (Fear2Fear) |
 |
fixme (Hackerspace Lausanne) |
 |
fluxfingers (Ruhr-Universitaet Bochum) |
 |
foobar5 (FH Aachen) |
 |
fuffateam (UNIMI) |
 |
garage4hackers (www.garage4hackers.com) |
 |
geek (N/A) |
 |
glimpses of grandeur (None) |
 |
h34dump (NSU) |
 |
h4x0rpsch0rr (TU Muenchen) |
 |
hackademics (University of Applied Sciences Offenburg) |
 |
hacknam style (KULeuven) |
 |
ham@eur (None) |
 |
hax.ko (Universität Koblenz) |
 |
helpdeskman (Franklin University) |
 |
hexcellents (University Politehnica of Bucharest) |
 |
honeypot (Vladimir State University) |
 |
hyoub9un (hyoub9un) |
 |
ijustwannafly (XDU) |
 |
insanity (University) |
 |
jgor (University of Texas at Austin) |
 |
jhdxr (jhdxr) |
 |
kernel sanders (University of Florida) |
 |
keva (TUSUR) |
 |
knightsec (University of Central Florida) |
 |
koibastard (SSAU) |
 |
ksec (kmasecurity.net) |
 |
lobotomy (-) |
 |
m4khm4l (sharif university) |
 |
mma (The University of Electro-Communications) |
 |
mochigoma (Japan) |
 |
more smoked leet chicken (MSLC) |
 |
movsx (-) |
 |
mylittleexploit (CU Boulder) |
 |
n0nfl4gs (India) |
 |
null life (NULL) |
 |
nullify (University of Nebraska at Omaha) |
 |
opsec (Kerala University) |
 |
pax.mac team (Pax.Mac Team) |
 |
peakchaos (UCCS) |
 |
peterpen (SPbSU) |
 |
rentjong (id.ctfclub) |
 |
rooterx (Chlyabinsk State University) |
 |
rpisec (Rensselaer Polytechnic Institute) |
 |
sec0d (sec0d) |
 |
secup (FIT-HCMUP) |
 |
securinets (securinets) |
 |
sesi (National University of Mongolia) |
 |
shadow cats (Shadow Cats) |
 |
sibears (Tomsk State University) |
 |
sigma (sigma) |
 |
singleman (N/A) |
 |
squareroots (University Mannheim) |
 |
stratum auhuur (-) |
 |
tasteless (/) |
 |
team pong (-) |
 |
teamredace (Sogeti Netherlands) |
 |
the cat is #1!! (Kim Jong U) |
 |
the one (MEPHI) |
 |
thufir's heros (Ahmy) |
 |
tracer tea (Loosely) |
 |
trashthestack (None) |
 |
trex (NPP Gamma) |
 |
ufologists (Southern Federal University) |
 |
umd cyber team (University of Maryland, College Park) |
 |
utacsec (University of Texas at Arlington) |
 |
vanqeri (MIT) |
 |
vorpal (University of Tennessee, Knoxville) |
 |
w3stormz (-) |
 |
wizardsofdos (TU Darmstadt) |
 |
zanzibar (emerald city) |
 |
zensecurity (Digital Buddha University) |
 |
zolmeister (Zolmeister) |
Links
- rwthCTF 2012 website
- rwthCTF 2011 website
- Detailled report from rwthCTF 2011
- rwthCTF Google Group
- Research Group IT-Security, RWTH Aachen University
- CIPHER - discontinued series of CTFs by i4 @ RWTH Aachen
- DEFCON - without a doubt the most demanding CTF
- iCTF - very creative and constantly changing CTF series
- ruCTF - a well-known series of CTFs
Contact
Research Group IT-SecurityRWTH Aachen University
Aachen, Germany
Mail: rwthrwthctf.heipei.io
Web: https://itsec.rwth-aachen.de
IRC: #rwthCTF@freenode
Twitter: @0ldEur0pe